As organizations increasingly depend on data to drive decision-making, securing that data has become a top priority. SQL Server, as a full-featured relational database management system, offers robust security mechanisms. However, the effectiveness of these mechanisms depends on how well administrators configure and enforce them.
This article explores SQL Server’s three pillars of security: authentication, authorization, and encryption. Understanding and implementing these correctly ensures sensitive information remains protected, compliance requirements are met, and systems remain resilient against internal and external threats.
The Three Pillars of SQL Server Security
- Authentication – Verifying the identity of users or applications attempting to connect.
- Authorization – Controlling what authenticated users can access and modify.
- Encryption – Protecting data in transit and at rest from unauthorized viewing.
Together, these provide a layered defense strategy.
Authentication in SQL Server
SQL Server supports two primary modes of authentication:
- Windows Authentication
- Leverages Active Directory (AD) or local Windows accounts.
- Provides integrated security with Kerberos or NTLM protocols.
- Recommended for enterprise environments where domain control is available.
- SQL Server Authentication
- Uses SQL logins stored within SQL Server.
- Requires usernames and passwords.
- Useful for non-domain environments or cross-platform connections.
Best Practice: Use Windows Authentication whenever possible. Enable SQL Authentication only if necessary, and enforce strong password policies.
Configuring Authentication
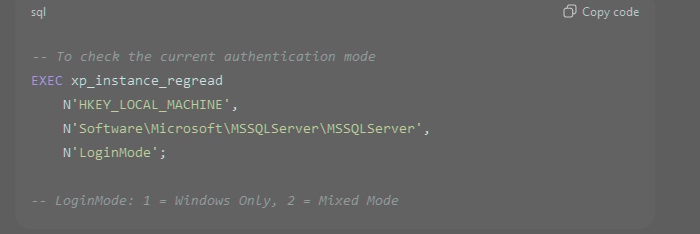
Authorization in SQL Server
Once authenticated, users must be assigned appropriate permissions. SQL Server provides a role-based access control (RBAC) model. If you need, see how to choose the no-code platform for your business.
- Server-Level Roles
- Control access at the server level (e.g., sysadmin, securityadmin, dbcreator).
- Database-Level Roles
- Control access within a database (e.g., db_owner, db_datareader, db_datawriter).
- Custom Roles
- Tailored roles to enforce principle of least privilege
Best Practice:
- Avoid granting sysadmin to application accounts.
- Assign roles rather than individual permissions for easier management.
- Review permissions regularly.
Example: Creating a Custom Role
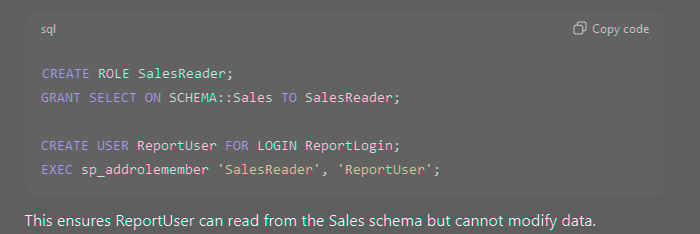
Encryption in SQL Server
SQL Server provides multiple encryption mechanisms to protect data:
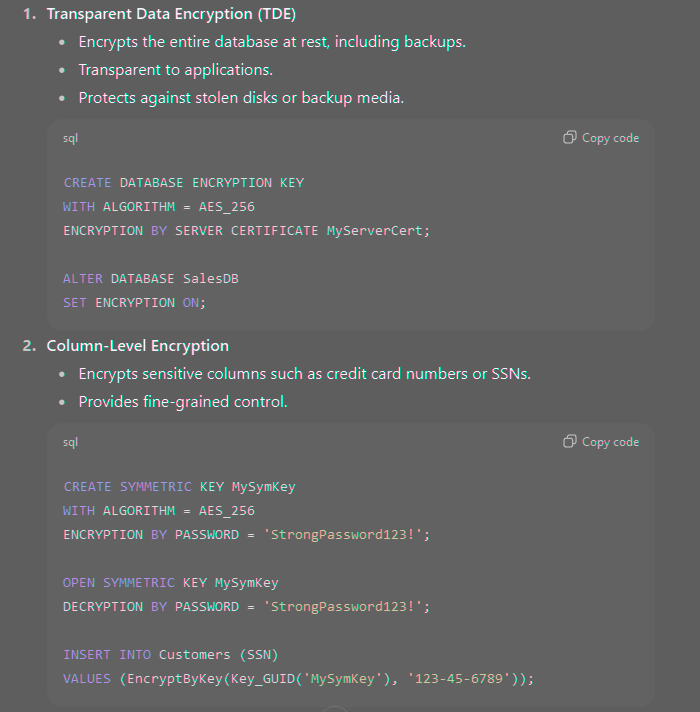
- Always Encrypted
- Designed for highly sensitive data.
- Encryption and decryption occur in the client application, not SQL Server.
- Protects data from DBAs or system admins.
- Encryption in Transit
- SQL Server supports TLS to encrypt data as it travels between client and server.
- Requires SSL/TLS certificates and proper configuration in SQL Server Configuration Manager.
Security Best Practices
- Principle of Least Privilege
- Users and applications should only have the access required to perform their roles.
- Secure sa Account
- Disable or rename the
saaccount if not required.
- Disable or rename the
- Enforce Strong Password Policies
- Require complexity, expiration, and lockouts.
- Enable Auditing and Logging
- Use SQL Server Audit or Extended Events to monitor security activity in Enterprise MediaWiki without downtime.
- Regular Patch Management
- Keep SQL Server updated with the latest cumulative updates and service packs.
- Separate Duties
- Divide responsibilities among DBAs, developers, and security officers to reduce insider threats.
Monitoring and Auditing
SQL Server offers built-in features for monitoring security:
- SQL Server Audit – Captures security-related events (e.g., failed logins, schema changes).
- Extended Events – Lightweight monitoring for suspicious activity.
- Dynamic Management Views (DMVs)
These tools enable organizations to maintain visibility and digital transformation into who is accessing data and how.
Example: Securing a Finance Database
Scenario: A company stores payroll information in SQL Server. Requirements include strong access control, encrypted data, and audit trails.
Implementation:
- Enable Mixed Mode authentication but restrict SQL logins.
- Create a custom role
PayrollViewerwith SELECT access only. - Use TDE to encrypt the entire database.
- Apply column-level encryption to Salary and BankAccount fields.
- Enable auditing to log all SELECT queries against sensitive tables.
This layered approach ensures confidentiality, integrity, and accountability.
Hands-On Exercise
- Enable TDE on a sample database.
- Create a custom database role with read-only access.
- Encrypt a column using symmetric key encryption.
- Query encrypted data and practice decryption using authorized keys.
This demonstrates authentication, authorization, and encryption in action.
SQL Server security is not a single feature but a multi-layered defense strategy. By configuring authentication properly, applying granular authorization, and implementing encryption for both data at rest and in transit, organizations can protect their most valuable asset: data.
For beginners, these concepts establish a foundation for safe database practices. For enterprises, they form a critical part of compliance frameworks such as GDPR, HIPAA, and PCI-DSS. Mastering SQL Server security ensures systems remain both functional and trustworthy in an increasingly data-driven world.









